Sometimes you just must follow that rabbit down the hole!
It was just a simple exercise to demonstrate a DNS name error response that lead to a really fun process of following a set of malicious HTTP redirections in a trace file. Splendid!
Grab sec-getsplendid.pcapng and follow along with me!
The Initial Goal
It was during a simple training session that this rabbit hole appeared. I simply wanted to start a Wireshark capture session, type in some crazy domain name in my browser, and show the DNS name error in the trace file.
Suddenly I was viewing a very sketchy website. Not what I’d expected from this exercise.


As soon as the page came up, I was thrilled! The URL had nothing in common with the name I’d typed in — I knew there must be a redirection in that trace file!
Little did I know how many twists and turns my host would take on its journey towards the «splendid» site.
HTTP Redirection Overview
HTTP redirections are not uncommon. They may be as simple as redirecting you from [something].com to www.[something].com. They aren’t always malicious, but they are worth watching.
HTTP redirections can easily be detected in a trace file. They consist of an HTTP response code beginning with 3. The list of registered HTTP response codes can be found at https://www.iana.org/assignments/http-status-codes/http-status-codes.xhtml.
Below is the list of the 3xx redirection codes.
300 Multiple Choices [RFC7231, Section 6.4.1]
301 Moved Permanently [RFC7231, Section 6.4.2]
302 Found [RFC7231, Section 6.4.3]
303 See Other [RFC7231, Section 6.4.4]
304 Not Modified [RFC7232, Section 4.1]
305 Use Proxy [RFC7231, Section 6.4.5]
306 (Unused) [RFC7231, Section 6.4.6]
307 Temporary Redirect [RFC7231, Section 6.4.7]
308 Permanent Redirect [RFC7538]
In our trace file, you will see 301 and 302 response codes during the malicious redirection process.
The first redirection is illustrated below.
[See frames 12, 14, and 15 in sec-getsplendid.pcapng.]


You can quickly detect HTTP redirections using this simple display filter:
http.response.code > 299 && http.response.code < 400
Where Did We Go?
Applying the display filter shown above and adding a column for the HTTP location field, we can easily see how our client was bounced around on a path to the getsplendidapps site.


A Redirection Profile
You may notice that my redirection packets are colored with a bright blue background. I’ve created a Wireshark profile for HTTP redirections. My profile contains numerous columns and a button to detect HTTP redirections.
You can download my profile here.
Need help installing this profile on your Wireshark system? Check out the blog, «Get my Troubleshooting Profile,» for instructions.
Annotations Galore!
Here’s where I had a fun time with this trace file. I went through the file packet by packet to annotate the redirection processes.
Click the Capture File Properties button (lower left corner, next to the Expert button) to bring up the Capture File Properties window. Scroll down in the upper portion of the window to see all of my annotations, as shown below.
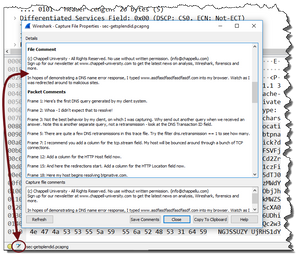

Create a Redirection Report
This is how I create reports of my analysis findings. I right click on packets of interest in the Packet List pane and add comments during my analysis sessions. When completed, I click and drag over the contents in the Capture File Properties window to create a cool report of my findings.
Download my report here.
Enjoy!
-Laura
WANT TO LEARN MORE? We offer on-demand, online and instructor-led courses on Wireshark and TCP/IP communications! Check out the links under «Training» on the menu for more information!
Sign up for our biweekly newsletter to know when future blogs, events, or freebies are announced. Every new sign up also gets five free labs!

 26 февраля, 2021
26 февраля, 2021  kevich
kevich  Опубликовано в рубрике
Опубликовано в рубрике